CYBER SECURITY
Helping you identify
threats in business.
We automate processes, move data, and keep your software tools working in harmony.
Creating workflows that do busywork for you—so you can get more done. Use your old
utilities like Gmail/ Slack/ CRM and integrate with Zapier.
Complete control
and
transparency.
We do the work, but you own the decisions. This means you control how and when potential incidents are escalated, what response actions (if any) you want us to take, and who should be included in communications. Weekly and monthly reports let you know what is happening in your environment and what steps have been taken to keep you safe.
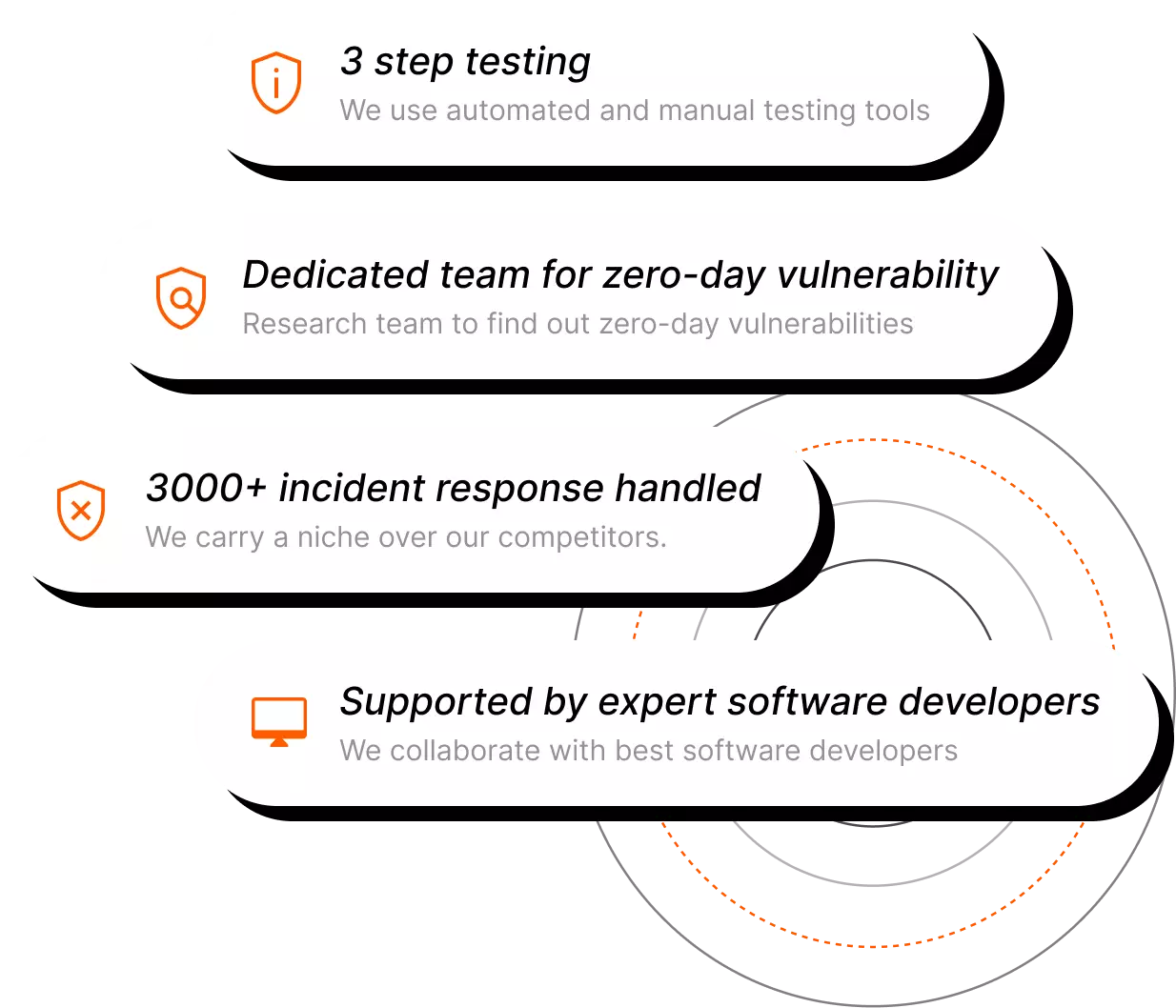
Notify
We notify you about the detection and provide details to help you with prioritization and response.
Collaborate
We work with your internal team or external point(s) of contact to respond to the detection.
Authorize
We handle containment and neutralization actions and inform you of the action(s) taken.
Domains we've worked with
FOOD AND SERVICES
EDUCATION AND E-LEARNING
AUTOMOBILE INDUSTRY
HEALTHCARE
TRAVEL
BANKS
GAMING
E-COMMERCE
We orchestrate digital solutions

High - fidelity detection
We combine deterministic and machine learning models to spot suspicious behaviors and the tactics.

Elite
expertise
Our highly-trained team of threat hunters, engineers, and ethical hackers has your back 24/7.

Outcome focused security
Every hunt, investigation, and response action results in decision-driving data.
Technologies we work on







